A basic principle of security is to expose as little attack vectors as possible. The more different ways to hit our infrastructure, the harder it will be to protect it. Thus, I always block the MySQL port (3306) by default.
This means, however, that direct connection from our PC to the MySQL or MariaDB database is not possible. Some people whitelist their own IPs on the firewall, howeverr, this is not practical. Instead, we will create what is known as a SSH Tunnel.
SSH Tunnels work by logging in normally through SSH, just as you would when using Putty, and using this connection to log in to MySQL, which will see it as if it were a local connection.
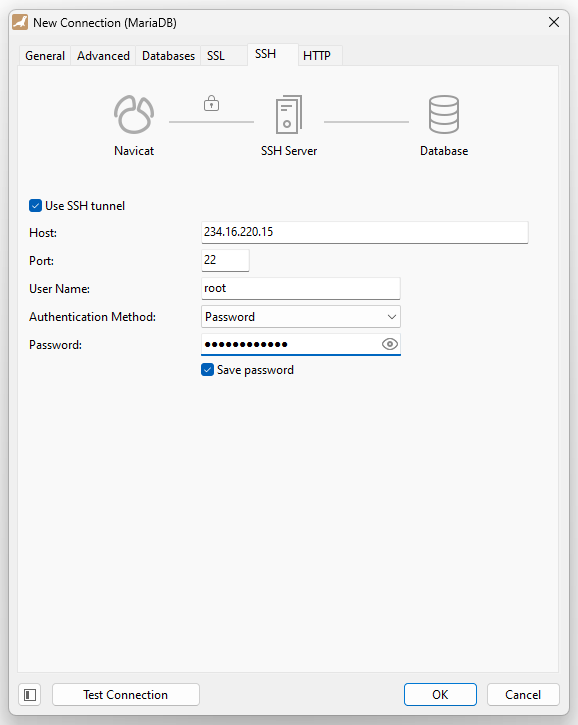
Here is how you set it up – Host is the host of your server. Choose Private Key or Password as aproppiate.
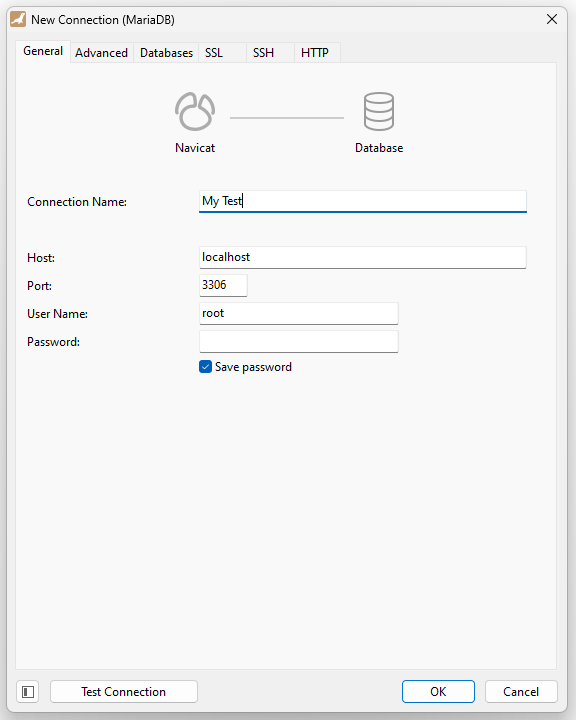
On the General tab we will configure it as if it were a local connection. Note that the root user can login with no password in MariaDB – this is no security issue as we are root already anyway.
Note that Navicat is problematic when it comes to SSH keys – if you get some error about cyphers, try updating to a newer Navicat version. If it complains about the SSH Key or PPK file version being too new, load your SSH Key into puttygen.exe (a free tool included with Putty), choose “Parameters for saving key files” from the Key menu and set the PPK Version to 2. Finally save the ppk file and use that in Navicat.
Leave a Reply